Cloud computing environments provide enhanced scalability and flexibility to IT organizations. Many options exist for building cloud strategies, public, private etc. For many companies private cloud is an attractive option because it allows them to maintain full visibility and control of their IT systems. Private clouds can also be further enhanced by merging private cloud systems with public cloud systems in a hybrid cloud. This allows some systems to gain the economies of scale offered by public cloud while others are maintained internally. Some great examples of hybrid strategies would be:
- Utilizing private cloud for mission critical applications such as SAP while relying on public cloud for email systems, web hosting, etc.
- Maintaining all systems internally during normal periods and relying on the cloud for peaks. This is known as Cloud Bursting and is excellent for workloads that cycle throughout the day, week, month or year.
- Utilizing private cloud for all systems and capacity while relying on cloud based Disaster Recovery (DR) solutions.
Many more options exist and any combination of options is possible. If private cloud is part of the cloud strategy for a company there is a common set of building blocks required to design the computing environment.
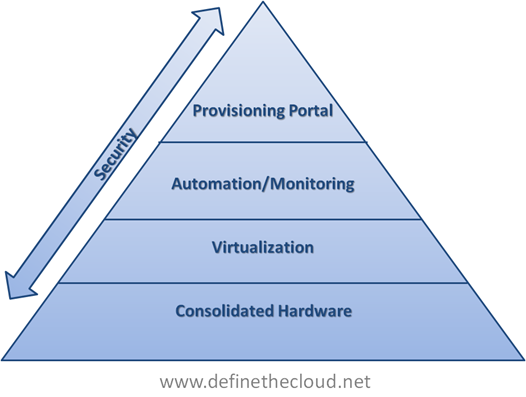
In the diagram above we see that each component builds upon one another. Starting at the bottom we utilize consolidated hardware to minimize power, cooling and space as well as underlying managed components. At the second tier of the private cloud model we layer on virtualization to maximize utilization of the underlying hardware while providing logical separation for individual applications.Â
If we stop at this point we have what most of today’s data centers are using to some extent or moving to. This is a virtualized data center. Without the next two layers we do not have a cloud/utility computing model. The next two layers provide the real operational flexibility and organizational benefits of a cloud model.
To move out virtualized data center to a cloud architecture we next layer on Automation and Monitoring. This layer provides the management and reporting functionality for the underlying architecture. It could include: monitoring systems, troubleshooting tools, chargeback software, hardware provisioning components, etc. Next we add a provisioning portal to allow the end-users or IT staff to provision new applications, decommission systems no longer in use, and add/remove capacity from a single tool. Depending on the level of automation in place below some things like capacity management may be handled without user/staff intervention.
The last piece of the diagram above is security. While many private cloud discussions leave security out, or minimize its importance it is actually a key component of any cloud design. When moving to private cloud customers are typically building a new compute environment, or totally redesigning an existing environment. This is the key time to design robust security in from end-to-end because you’re not tied to previous mistakes (we all make them)or legacy design. Security should be part of the initial discussion for each layer of the private cloud architecture and the solution as a whole.
Private cloud systems can be built with many different tools from various vendors. Many of the software tools exist in both Open Source and licensed software versions. Additionally several vendors have private cloud offerings of an end-to-end stack upon which to build design a private cloud system. The remainder of this post will cover three of the leading private cloud offerings:
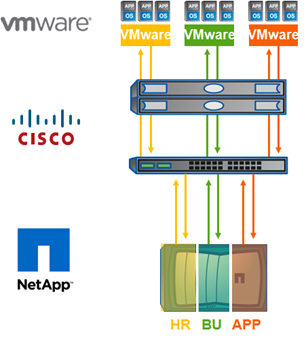
- Secure-Multi-Tenancy (NetApp, VMware, Cisco) (http://www.imaginevirtuallyanything.com/)
- Matrix (HP) (http://h18004.www1.hp.com/products/blades/components/matrix/main.html)
- Vblock (EMC, VMware, Cisco) (http://vcecoalition.com/solutions.htm)
Scope: This post is an overview of three excellent solutions for private cloud. It is not a pro/con discussion or a feature comparison. I would personally position any of the three architectures for a given customer dependant on customer requirements, existing environment, cloud strategy, business objective and comfort level. As always please feel free to leave comments, concerns or corrections using the comment form at the bottom of the post.
Secure Multi-Tenancy (SMT):
Vendor positioning: ‘This includes the industry’s first end-to-end secure multi-tenancy solution that helps transform IT silos into shared infrastructure.’
SMT is a pairing of: VMware vSphere, Cisco Nexus, UCS, MDS, and NetApp storage systems. SMT has been jointly validated and tested by the three companies, and a Cisco Validated Design (CVD) exists as a reference architecture. Additionally a joint support network exists for customers building or using SMT solutions.
Unlike the other two systems SMT is a reference architecture a customer can build internally or along with a trusted partner. This provides one of the two unique benefits of this solution.
Unique Benefits:
- Because SMT is a reference architecture it can be built in stages married to existing refresh and budget cycles. Existing equipment can be reutilized or phased out as needed.
- SMT is designed to provide end-to-end security for multiple tenants (customers, departments, or applications.)
HP Matrix:
Vendor positioning: ‘The industry’s first integrated infrastructure platform that enables you to reduce capital costs and energy consumption and more efficiently utilize the talent of your server administration teams for business innovation rather than operations and maintenance.’
Matrix is a integration of HP blades, HP storage, HP networking and HP provisioning/management software. HP has tested the interoperability of the proven components and software and integrated them into a single offering.Â
Unique benefits:
- Of the three solutions Matrix is the only one that is a complete solution provided by a single vendor.
- Matrix provides the greatest physical server scalability of any of the three solutions with architectural limits of thousands of servers.
Vblock:
Vendor positioning: ‘The industry’s first completely integrated IT offering that combines best-in-class virtualization, networking, computing, storage, security, and management technologies with end-to-end vendor accountability.’
Vblocks are a combination of EMC software and storage storage, Cisco UCS, MDS and Nexus, and VMware virtualization. Vblocks are complete infrastructure packages sold in one of three sizes based on number of virtual machines. Vblocks offer a thoroughly tested and jointly supported infrastructure with proven performance levels based on a maximum number of VMs.Â
Unique Benefits:
- Vblocks offer a tightly integrated best-of-breed solution that is purchased as a single product. This provides very predictable scalability costs when looked at from a C-level perspective (i.e. x dollars buys y scalability, when needs increase x dollars will be required for the next block.)
- Vblock is supported by a unique partnering between Cisco, EMC and VMware as well as there ecosystem of channel partners. This provides robust front and backend support for customer before during and after install.
Summary:
Private cloud can provide a great deal of benefits when implemented properly, but like any major IT project the benefits are greatly reduced by mistakes and improper design. Pre-designed and tested infrastructure solutions such as the ones above provide customers a proven platform on which they can build a private cloud.

Great post, I totally agree with what was said
I like the pyramid diagram however I think of it differently now
After seeing most organizations follow it (as well as myself and my previous org), with hindsight…
I feel that monitoring is the very first step, this way you have proof of where you success is as well as your failures this will help accelerate/snowball all higher layers in the pyramid, I really wished I had better trending historical data prior to virtualization and consolidation. Once I had that usage monitoring setup building internal clouds was a no brainier to anyone technical, financial, or politically minded.
Also virtualization is before consolidation as it makes workloads more portable and much easier to consolidate both in tech, finance, and political arenas.
When I envision that pyramid… top to bottom
provisioning followed by self provisioning
automation followed by orchestration
Consolidation (compute, interconnect, store)
Virtualization (compute, interconnect, store)
Usage Monitoring/Trending (aka metering.. as we are all doing fault monitoring already… right??)
And of course following a proper security circle
Patrick,
Thanks for the feedback and insight, I like the way your envisioning the process. My diagram was intended to show the building layers, stacking upon one another to create a cloud computing environment from a traditional datacenter. In that process I see consolidating the hardware, virtualizing it, applying automation and monitoring tools accross the board, and lastly building in a provisioning portal. This is a common migration path that meshes well with existing hadrware cycles.
I definitely agree that you need to ensure ways to monitor and quantify successes and failures during the entire process. It would be better to know you’re headed down the wrong path early on, rather than after all is said and done.
Thanks for the feedback!
interesting read
Hi Joe,
Can you differentiate your expression “Of the three solutions Matrix is the only one that is a complete solution provided by a single vendor” form expression “Vblocks offer a tightly integrated best-of-breed solution that is purchased as a single product. This provides very predictable scalability costs when looked at from a C-level perspective (i.e. x dollars buys y scalability, when needs increase x dollars will be required for the next block.)
Vblock is supported by a unique partnering between Cisco, EMC and VMware as well as there ecosystem of channel partners. This provides robust front and backend support for customer before during and after install.”?
Dan,
Thanks for reading and the question. The HP Matrix system is the only one of the three that contains hardware and software all sourced from a single vendor. With Vblock VCE puts all the components together and ships them as a single product but underneath you’ve got three vendors components. Which is better or worse is open for debate. Single vendor would be argued as tighter coupling and better support, where mulit-vendor would be argued as ‘best-of-breed’ products. In my opinion they both have their uses.
Joe
Hi would you mind letting me know which webhost you’re using?
I’ve loaded your blog in 3 completely different browsers and I must say this blog loads a lot quicker then most.
Can you suggest a good web hosting provider at a honest price?
Thanks a lot, I appreciate it!