In an attempt to clarify my future posts I will begin categorizing a bit. The following post will be part of a Technical Deep Dive series.
Fibre Channel over Ethernet (FCoE) is a protocol designed to move native Fibre Channel over 10 Gigabit Ethernet and above links, I’ve described the protocol in a previous post (http://www.definethecloud.net/?p=80.) In order for FCoE to work we need a mechanism to carry the base Fibre Channel port / device login mechanisms over Ethernet. These are the processes for a port to login and obtain a routable Fibre Channel Address. Let’s start with some background and definitions:
| DCB | Data Center Bridging |
| FC | Native Fibre Channel Protocol |
| FCF | Fibre Channel Forwarder (an Ethernet switch capable of handling Encapsulation/De-encapsulation of FCoE frames and some or all FC services) |
| FCID | Fibre Channel ID (24 Bit Routable address) |
| FCoE | Fibre Channel over Ethernet |
| FC-MAP | A 24-Bit value identifying an individual fabric |
| FIP | FCoE Initialization Protocol |
| FLOGI | FC Fabric Login |
| FPMA | Fabric Provided MAC Address |
| PLOGI | FC Port Login |
| PRLI | Process Login |
| SAN | Storage Area Network (switching infrastructure) |
| SCSI | Small Computer Systems Interface |
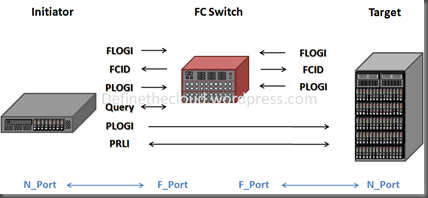
When a node comes online it’s port is considered an N_port. When an N_port connects to the SAN it will connect to a switch port defined as a Fabric Port F_Port (this assumes your using a switched fabric.) All N_ports operate the same way when they are brought online:
- FLOGI – Used to obtain a routable FCID for use in FC frame exchange. The switch will provide the FCID during a FLOGI exchange.
- PLOGI – Used to register the N_Port with the FC name server
At this point a targets (disk or storage array) job is done, they can now sit and wait for requests. An initiator (server) on the other hand needs to perform a few more tasks to discover available targets:
- Query – Request available targets from the FC name server, zoning will dictate which targets are available.
- PLOGI – A 2nd port Login, this time into the target port.
- PRLI – Process login to exchange supported upper layer protocols (ULP) typically SCSI-3.
Once this process has been completed the initiator can exchange frames with the target, i.e. the server can write to disk.
FIP:
The reason the FC login process is key to understanding FIP is that this is the process that FIP is handling for FCoE networks. FIP allows an Ethernet attached FC node (Enode) to discover existing FCFs and supports the FC login procedure over 10+GE networks. Rather than just providing an FCID, FIP will provide an FPMA which is a MAC address comprised of two parts: FC-MAP and FCID.
48 bit FCMAP (Mac Address)
FIP
So FIP provides an Ethernet MAC address used by FCoE to traverse the Ethernet network which contains the FCID required to be routed on the FC network. FIP also passes the query and query response from the FC name server. FIP uses a separate Ethertype from FCoE and its frames are standard Ethernet size (1518 Byte 802.1q frame) whereas FCoE frames are 2242 Byte Jumbo Frames.
FIP Snooping:
FIP snooping is used in multi-hop FCoE environments. FIP snooping is a frame inspection method that can be used by FIP snooping capable DCB devices to monitor FIP frames and apply policies based on the information in those frames. This allows for:
- Enhanced FCoE security (Prevents FCoE MAC spoofing.)
- Creates FC point-to-point links within the Ethernet LAN
- Allows auto-configuration of ACLs based on name server information read in the FIP frames
FIP Snooping
Summary:
FIP snooping uses dynamic Access Control Lists to enforce Fibre Channel rules within the DCB Ethernet network. This prevents Enodes from seeing or communicating with other Enodes without first traversing an FCF.
Feedback, corrections, updates, questions?


Comments (55)